
Published On: 04 Sep 2021

SQL Injection + XSS In US Department of Health and Human Services Website
SQL Injection
General | Web
---
HIGH VALIDDescription
While searching for XSS on the US Department of Health and Human Service website (I did find one) I noticed something strange in a "Select" inside a search form when I add a some characters after its value using "Inspect Element -> Network Tab". It turned out later that it was the result of an XSS and SQL injection vulnerabilities in just one place.
Impact
SQL injection vulnerability leads to a leak of sensitive data in 3 databases from https://hhs.gov . XSS vulnerability may leads to steal user data, browser sessions, malicious redirection and more (combined with social engineering techniques).
Reproduction Steps
Step
1
I visit a subdomain in https://hhs.gov lets call it: sub
I tested a search form with method = POST but it has some GET parameters where the submited values are printed in the same page again after the submit is done.
Step
2
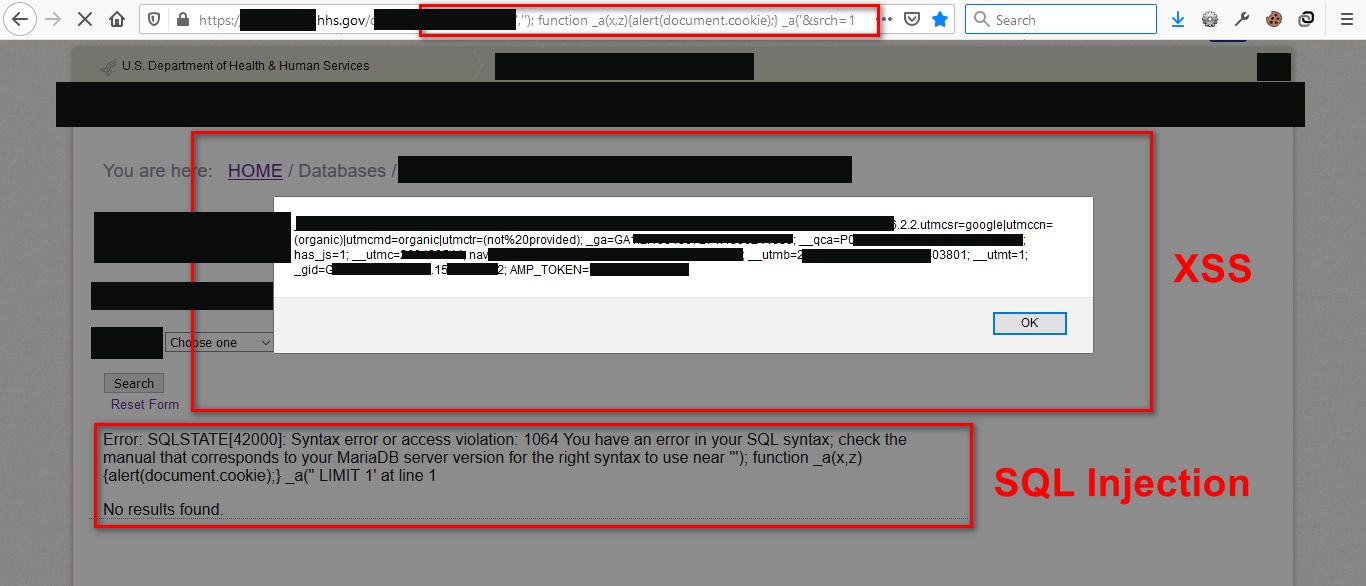
------ XSS ------
In the page, one of the submitted values is added to a JavaScript function inside the same page, lets call it: blabla() :
function blabla(){ ... } blabla('My_Submitted_Text_here', 'another param whatever');
What I did is to let the function to be called normally by adding this code: ',''); and a custom function called _a()
This function will take 2 dummy parameters like the function we targeted (random params names) in my case: x & z
Then I can call the function and complete the code like this:
function _a(x,z){ alert('WOW!'); } _a('
The goal is to let the function work normally without any errors and add a custom function with custom payload so the final code will become:
function blabla(){ ... } blabla('My_Query_Text_here',''); function_a(x,z){ alert('WOW!'); } _a('', 'another param whatever');
As you can see, I can pass any code inside the _a() function and it will be executed.
Step
3
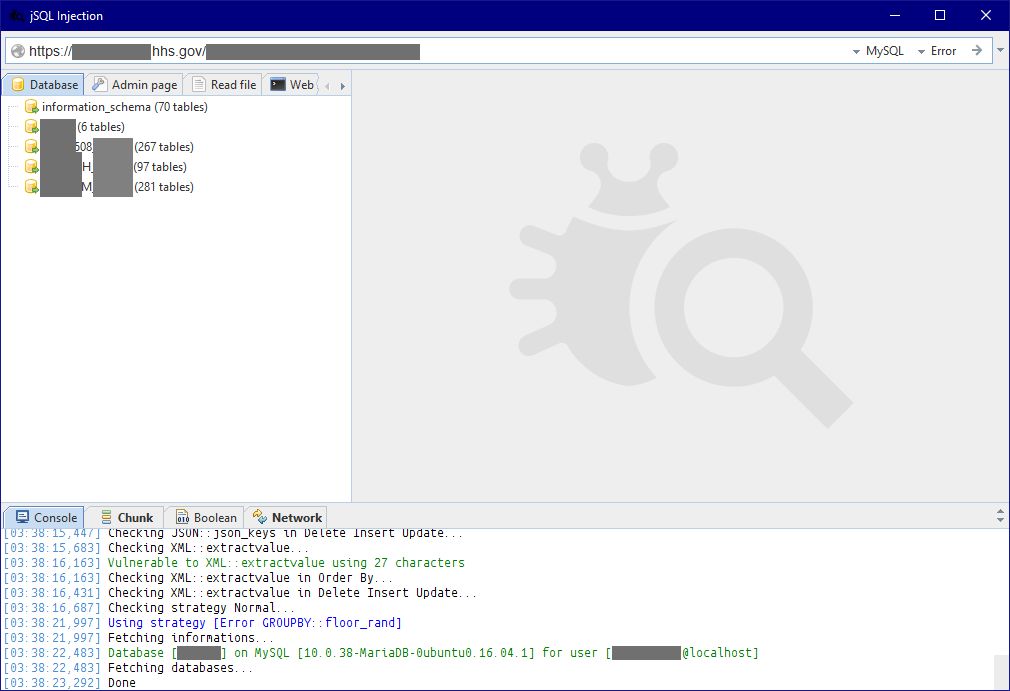
------ SQL Injection ------
The same XSS code was able to reveal another bug; SQL injection.
Since the SQL error was displayed as you can see in the image (from step #2), I use an automatic SQL injection tool to check the bug type and extract the databases as you can see in the attached image.
