
Published On: 28 Oct 2020

Reveal the page admin who create shop for the page
Privacy/Authentication
Facebook | Web
---
MEDIUM VALIDDescription
Admins of pages are able to create their “Shop” and publish their products using Commerce manager https://www.facebook.com/commerce_manager/ . A malicious user is able to reveal the “Name” of the creator of a “published” MiniShopStorefront,by passing the ID of the “MiniShopStorefront “ to a misconfigured GraphQl request which could lead to a page admin disclosure.
Impact
Anyone can reveal the page admin that published a MiniShopStorefront on the shop page by abusing a misconfigured GraphQL request.
Reproduction Steps
Step
1
The Victim creates a commerce manager account , and he add his page then publishing products to it .
The attacker will also create a commerce manager and try to add product ( this step is only to intercept the vulnarable request) .
Step
2
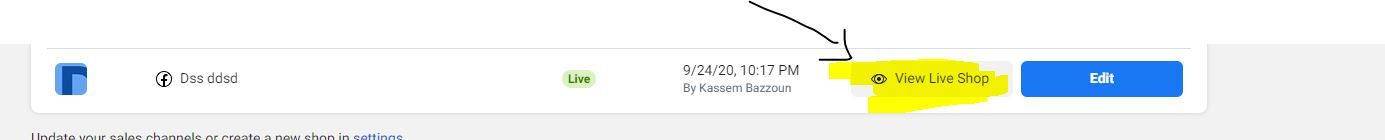
Now from the attacker side and after creating the Commerce and submitting /publishing the shop section, go to the “Shop” section in the menu navigation, beside the page a button will appeared “VIEW LIVE SHOP”
(See the attached image)
Step
3
So intercept the request, and Click on this button .
This request will contain some information about the shop version
Variables: {"storefrontID":"MINI_SHOP_STORE_FRONT_ID","includeLiveRevisionLimit":25}
Step
4
Attacker now , will enter to the shop of the Victim page , then he will get the shop id
( go to page source and search for :
"MiniShopStorefront","id":"ID HERE "
)
This is the id of the victim page that we wants to reveal its creator ( admin)
Step
5
From the GraphQl request taken in step nb 3 put the victim shop id
Variables: {"storefrontID":"VICTIM_SHOP_ID","includeLiveRevisionLimit":25}
response will be :
"storefront_workspace": {
"id": "331779768251880",
"version_history_revisions": {
"edges": [
{
"node": {
"creation_time": 1601028218,
"save_type": "MAJOR",
"revision_status": "PUBLISHED",
"revision_title": "Default revision",
"id": "360779901724650",
"revision_creator_name": "Kassem Bazzoun ",
"bi_information": {
"review_status": "ACCEPTED",
"pages_failed": 0,
"section_failed": 0
},
"__typename": "PAYShopRevision"
},
}
],
where revision_creator_name contain the name of the admin who create this shop
Step
6
Wait !? the response is not contain the id of this user !? we have only his name!
ok take this tips, I found a way to make sure who is the admin
simply attacker will block the real admin , once he block him the response will be
"revision_creator_name": "Facebook User ",
and as you know , "Facebook User" used when an account is disabled , or when you block someone on Facebook .
Step
7
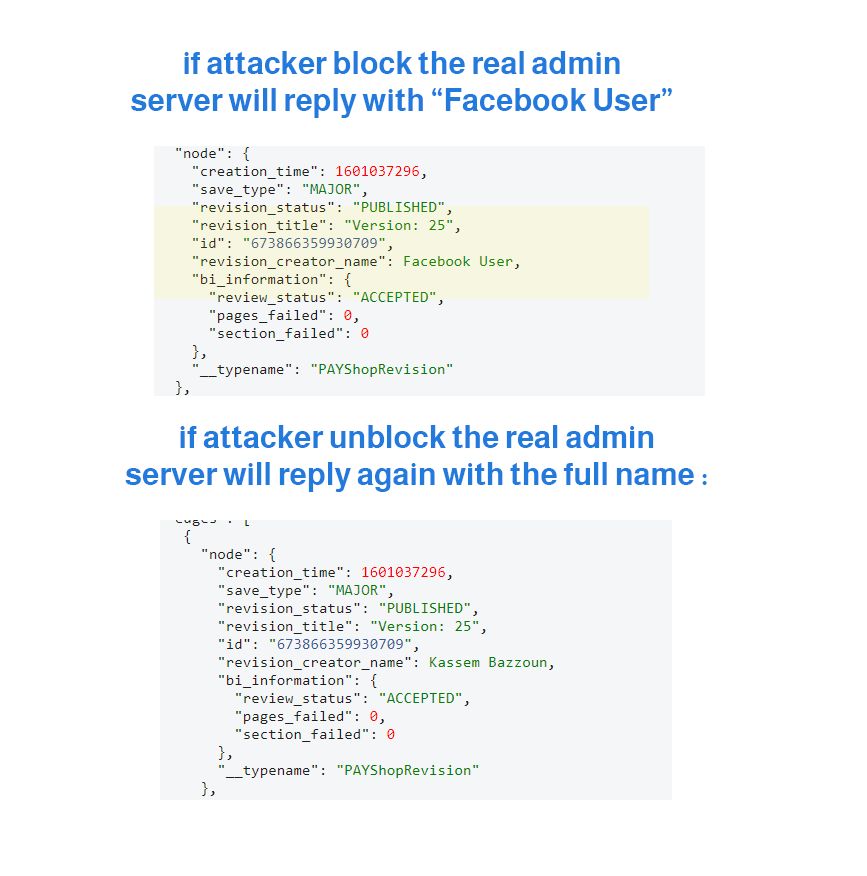
so to make sure 100% who is the admin , there is some request on Facebook that's responsible to fetch the id of user based on search by name , I found a request once i search for specific name it return an array contains the id of the users who have this name
Example : if you pass the name " Mark Zuckerberg" to this request , it will return [4,id,id,id]
then in this bug , since you have the full name of the admin who create the shop , just reveal the ids of users who have this name , and start blocking each id until you found the the response will return " Facebook User"
