
Published On: 30 Jan 2020

Page admin disclosure via the 'thread_associated_page_admin'
Privacy/Authentication
Facebook | Other
---
MEDIUM VALIDDescription
In Facebook pages there is an option that allow the managers of the page to assign a conversation to a specific admin. A malicious user is able to disclose the assigned admin to his message through the Graphql response responsible of fetching messages with someone .
Impact
Page admin disclosure via the 'thread_associated_page_admin' field when admin is assigned to a page conversation.
Reproduction Steps
Step
1
User A sent a message to the victim page .
Step
2
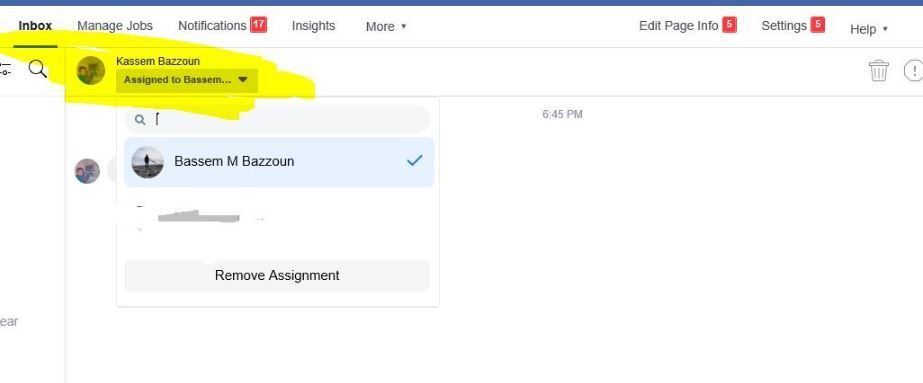
The message is received to the victim page page, " User B " is one of the admins, he assigned this message to another admin called " User C ", by entering to the inbox of his page and choose "User C" message and in the top of the page under the sender name -> "Assign Conversation"
Step
3
User A (attacker) wants to disclose the assigned admin on his message , so he will send a graphql request to fetch his message with this page( load messages from messenger) .
Step
4
Attached is the Graphql request to fetch message with someone
First party token (e.g. android token ) .doc_id : 2696825200377124
variables : {"id":"VICTIM_PAGE"}
Step
5
Looking at the response User A (attacker) is able to see an object contain the details of the assigned admin to his message and thus User A is able to disclose one of the page admins.
the object is " thread_associated_page_admin" contain the id of the admin, his name and his profile pic .
"id": "100036542018278",
"name": "Victim Name",
"profile_picture": { ... }
Thank
I would like to thanks my friends Sarmad Hassan & Rony K Roy for helping me in this bug . I advice you to read Sarmad & Rony Write-ups Sarmad : https://bugreader.com/jubabaghdad https://medium.com/@JubaBaghdad Rony : https://bugreader.com/rony
