
Published On: 13 May 2019

Add description to Instagram Posts on behalf of other users
IDOR
Instagram | Web
---
HIGH VALIDHello folks, it’s JubaBaghdad again, today I would like to share with you an interesting bug that I found in Instagram that make me able to add description to other users Posts, are you ready !! :)
Description

In 2018 Instagram added a new feature called "IGTV" for watching long-form, vertical video from your favorite Instagram creators, IGTV feature was vulnerable to IDOR bug and it allow the attacker to add description on other users posts that did not have one set.
Impact
* Add description on other users posts that don't have one set before. * It work in all kind of post, photos, video and IGTV posts. * It work on public accounts only, which means the attacker should be able to see the victim post.
Reproduction Steps
Step
1
From the attacker account go to https://www.instagram.com/[your-User-Name]/ and click on IGTV option and upload video then edit it.
Step
2
Once you edit your video intercept the request with Burpsuite, the request will be like below:
POST /media/1887820989027383407/edit/
caption=test&publish_mode=igtv&title=test
where "1887820989027383407" is the ID of the attacker media
and caption= refers to the description that you want to put on your post.
Step
3
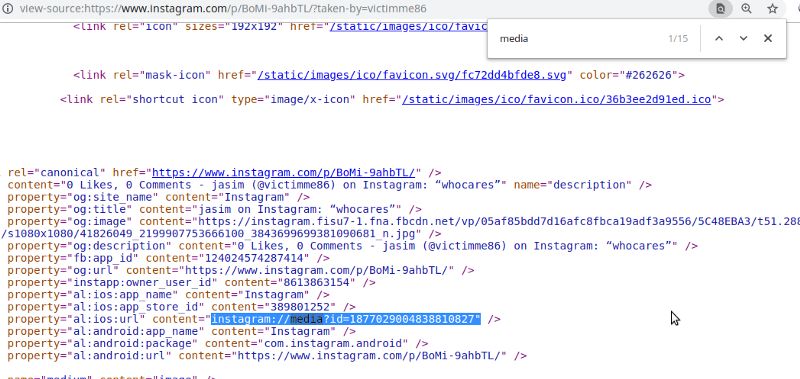
Go to any user post that don't have a description and get the media ID of that post from viewing the source code ( you can get the media id by hitting like button and intercept the request using burpsuite).
Step
4
Replace your media ID (Attacker) with other user post media ID (Victim).
Step
5
The response will give you an Internal Server error with an error message “Oops an error occurred” but that dosen't mean the bug didn't work.
Step
6
Refresh the page of other user post, Description is added by the attacker :).
Why this bug is consider as High!
* A lot of users (Millions of accounts) on Instagram set their profile to public . * If we search on any public account, we can find at least one post that have no description which make the bug works in almost millions of accounts. * If this bug was in a bad hands (Black hat), he can target the most-followed_Instagram_accounts, for example: Mark zuckerberg ===> 4.6 Millions Followers ==>https://www.instagram.com/p/aw9oRSQec-/?taken-by=zuck Lionel Messi ===> 97 Millions Followers ==>https://www.instagram.com/p/Bj2iTmAndC8/?taken-by=leomessi The list is so long :), so Imagine High bug like this in a bad hands, it could be leading to a big media hype by targeting celebrities as an example, or create big problems between giant companies like apple and its competitor Samsung :) and so on.
Thanks
I would like to thanks Facebook Security Team for this awesome Bounty. Also I would like to Thanks My friend Kassem Bazzoun for his huge support and helping me with this bug. Thanks a million bro. :)
Takeways:
1- Don’t depends on the response only, sometimes it gives you an error, but instead your bug will work, I learned that when I saw a video couple months ago of my friend Abdellah Yaala see his video https://www.youtube.com/watch?v=DvNHjh0EJNs at the minute 1:22, so you have to check what you’re testing from the web app. too. 2- Try to check your target from time to time and to check if there is any new option or feature (when there is a new feature there is a new bug). 3- Try to memorize your target options, it will make you identify any new option quickly just like I did :).

