
Published On: 30 May 2020

Bypass CSRF Protection Lead to Account Takeover
CSRF
Private | Web
---
HIGH VALIDI found this bug in a private program on Hackerone. Usually, when web applications implement Anti-CSRF Tokens I always try to bypass them. There are several ways to bypass Anti-CSRF Tokens.
Description
Here, the target website was implementing anti-csrf tokens on every POST action you do in the website, for example when inviting users to be admins or when modifying settings. Due to misconfigured implementation of those anti-csrf tokens I was able to bypass CSRF Protection by removing the csrf-token and its value which are found in the request in the form of `&token={token-value}`. So now you can easily generate the CSRF POC to invite yourself and send it to the victim to be an admin with him
Impact
Malicious attacker is able to bypass the CSRF Protection and invite himself to be an admin with the target victim ending up with successful account/application takeover.
Reproduction Steps
Step
1
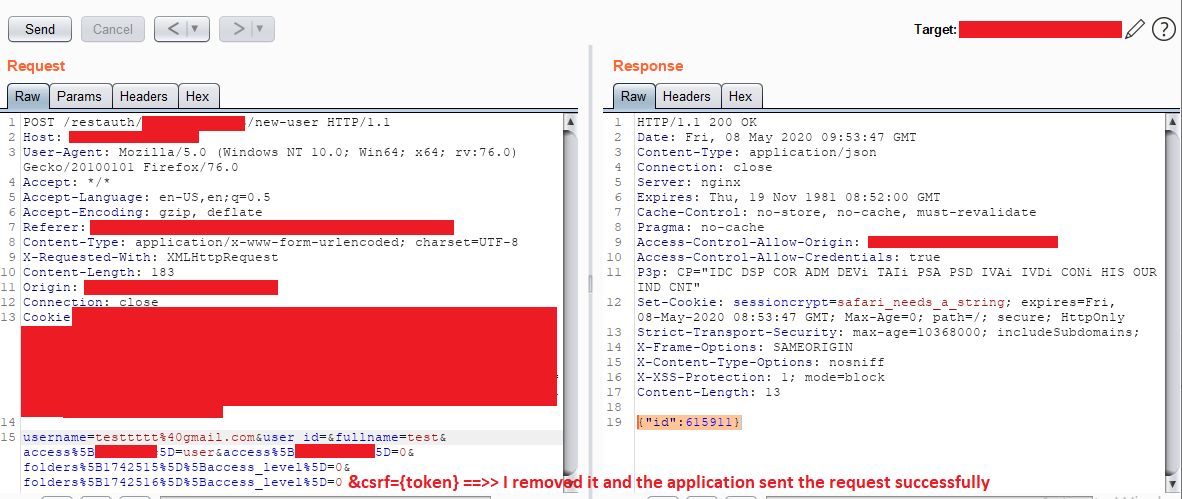
Enter your email and click invite.
Intercept the request.
Remove the csrf key and value from the request body (&token={token-value}).
Step
2
Generate a CSRF PoC and host it on web.
Step
3
Send the link to the victim.
When authenticated victim will click on the button. He will invite the attacker without his knowing.
Step
4
Attacker now will accept the invitation, so he will navigate to victim's application and kick him out and be the only admin for the target application ;)
Tips
When you see an anti-csrf token, always try to play around with it, sometimes it will lead to a potential vulnerability just like what happened with me.
Tricks to manipulate Csrf-Token
1. Try to remove the csrf key and value from the request body and forward it. 2. Try to enter a csrf token value that belongs to another user (by creating another test account). 3. Try keeping the csrf key and removing its value from the request body. You can try even more techniques.
