Published On: 25 Apr 2020

XSS in Express WiFi by Facebook
XSS
Facebook | Web
---
HIGH VALIDThe Express WiFi by Facebook has a "report problem" form using that a user can report any kind of issues he is facing while connecting to the internet. After raising a complaint, The express WiFi lands a user to thanks page. This Thanks Page was vulnerable to XSS. Vulnerable URL : *.expresswifi.com/customer/report_problem/?ref=retailer&customer_id&customer_mobile_number=9999999999&problem_types[0]=speed&success=1&back_uri=/home
Description
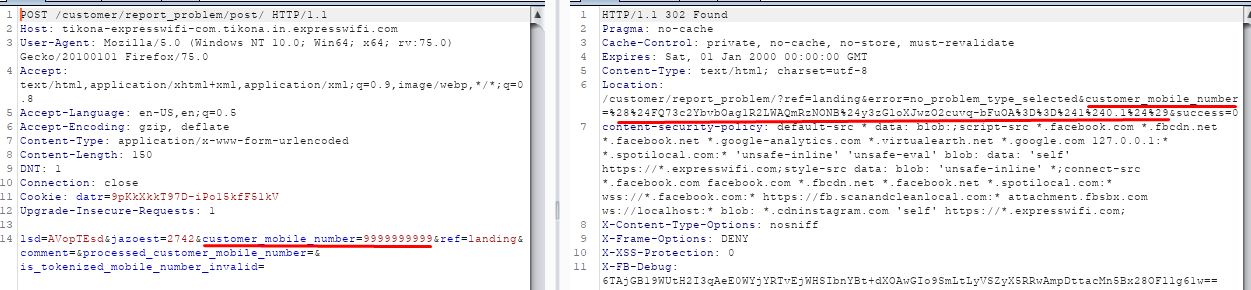
back_url parameter is used to redirect a user to home page after reporting the issue. It was filtering the harmful payload properly, There was no possible way to crack it. After few investigations, found that when user raise issue,It requires mobile number. And Mobile Number gets converted into encrypted format. I supplied XSS payload in mobile number field and It returned enc. format of payload. At last, I supplied enc. harmful payload to back_url parameter : pop-up appeared
Impact
Using XSS a malicious user could have stolen fb_dtsg(CSRF TOKEN), And could have make arbitrary requests on their behalf.
Reproduction Steps
Step
1
Go to : https://tikona-expresswifi-com.tikona.in.expresswifi.com/customer/report_problem
Step
2
Enter XSS payload in mobile number field.
Step
3
"What kinds of issues are you experiencing when using Express Wi-Fi?" : Don't select any option, It will return an error "Please select the option(s) that best describe your problem.", Also in the field of mobile number you will see an encrypted format of supplied payload.
Step
4
Final URL : *.expresswifi.com/customer/report_problem/?ref=retailer&customer_id&customer_mobile_number=9999999999&problem_types[0]=speed&success=1&back_uri=ENC_PAYLOAD_HERE